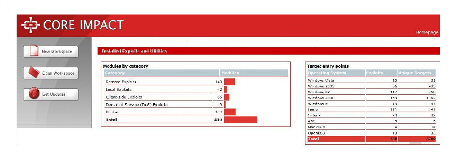
Security Audits
Our aim in security auditing is the formal examination and review of actions taken by system users. This process is necessary to determine the effectiveness of existing security controls, watch for system misuse or abuse by users, verify compliance with current security policies as well as a thorough detection of anomalies or intrusions.
Our IT Security audits are manual and systematic measurable technical assessments of a system or application.
Manual assessments include interviewing staff, performing security vulnerability scans, reviewing application and operating system access controls, and analyzing physical access to the systems.
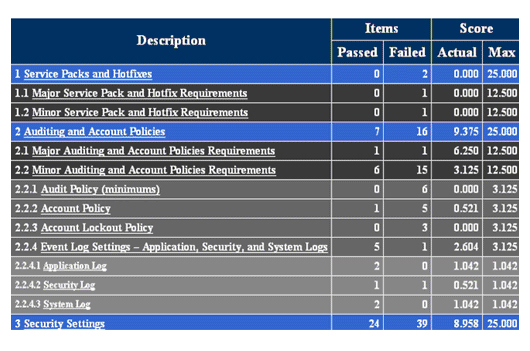
Automated assessments, or Computer Assisted Audit Techniques (CAAT), include system generated audit reports or using software to monitor and report changes to files and settings on a system. Systems can include personal computers, servers, mainframes, network routers, switches.
Applications can include Web Services, Microsoft Project Central and Oracle Database to name a few.